D – Link no longer sells the DNS-320 enclosure, but it is still supported on the product page. However, the latest firmware revision was released in 2016 and many known bugs can be used to compromise the equipment. On Thursday, scanning the malicious ELF binary on VirusTotal showed a minimum detection rate, with only one antivirus engine identifying Cr1ptT0r as a threat. At the time of publication, at least six antivirus engines pick up the malware.
Old firmware is issue
Details are scarce at the moment, a member of the Cr1ptT0r team has confirmed this to us, saying that D – Link DNS-320 NAS models have so many vulnerabilities that they should be built from scratch to improve things. Although it is known that old DNS-320 firmware versions are vulnerable to at least one bug that leads to remote code execution, a hard – coded backdoor for ShareCenter DNS-320L was published in 2018. Some Cr1ptT0r – affected users admitted to the installation of an outdated firmware version and that their device was exposed to the Internet at the time of the attack. The malware drops on the infected devices two plain text files. One is the ransom note called “FILES ENCRYPTED README.txt,” which gives the victim information on how to get more details about what happened and how to reach the ransomware operators in exchange for the key to the decryption of the file. The ransom note points the victim to the decryption service Cr1ptT0r, which contains the same contact details and the unlock key steps. The operators offer to unlock the first file free of charge to verify that they can decrypt the data. The other text file is called “cr1ptt0r support.txt” and stores a website address in the Tor network. This is a support URL that victims can provide if they lose what to do; if an infected device is online, it allows a remote shell. The member of the Cr1ptT0r group added that URLs and IP addresses were not logged, so there was no correlation between the data and the victim. Although the member of Cr1ptT0r says they only want to be paid and that spying is not on their agenda, they cannot guarantee privacy.
Synolocker decryption keys
The keys to unlock files are sold via the OpenBazaar marketplace for BTC 0.30672022 (approximately $ 1,200 at the current price of Bitcoin). There is also an option to pay less for the decryption of individual files. The cost is $ 19.99 and the encrypted file must be sent to be decrypted. A recent update to the OpenBazaar store page shows that Synolocker’s ransomware operator also offers the same price decryption keys. This ransomware strain caused serious damage back in 2014 when it infected Synology NAS servers that were running outdated DiskStation Manager versions with two vulnerabilities. Although the vendor released the patches at least eight months earlier, this was possible. In mid-2014, the crew behind Synolocker closed down their website and offered to sell in bulk all the unclaimed decryption key they had for 200 BTC (about $ 100,000 at the time), more than 5,500. When the website closes, the crew announced that all databases would be permanently deleted. Today, the ransomware handler told us that it is possible to match the private key that unlocks the data in the absence of a victim ID by brute – forcing, a process that is relatively fast in this case, with a few minutes to complete.
Files locked without any extension
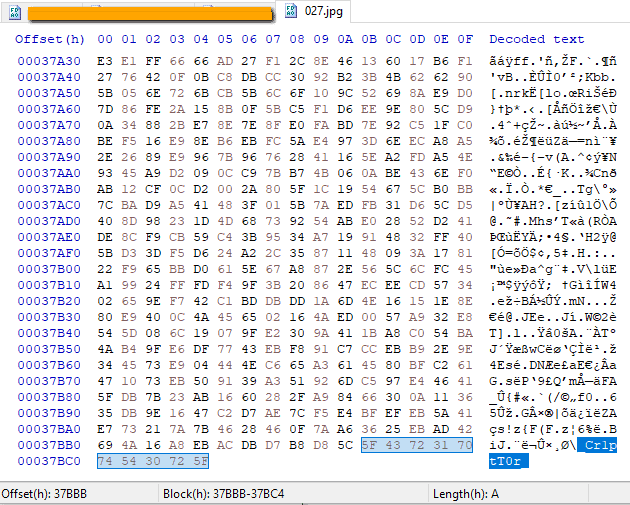
The ransomware, which is an ELF ARM binary, does not add a specific extension to the encrypted data, but security researcher Michael Gillespie did a brief analysis of the malware and its encrypted files and found that the end – of – file marker “Cr1ptT0r” was added.
File marker, h/t @demonslay335 He also says that the strings he noticed suggest that the Sodium crypto library is used by this ransomware strain and that the asymmetric encryption algorithm “curve25519xsalsa20poly1305″ is used. We received confirmation from the member of the Cr1ptT0r group with whom we spoke about these details. The public key (256-bit) used to encrypt the data is available in a separate file called”cr1ptt0r logs.txt,” which also contains a list of encrypted files, and is also attached to the end of the encrypted files, just before the marker. Gillespie says it matches the above encryption algorithm. The ransomware handler currently seems interested in targeting NAS devices that are popular with small companies for internally storing and sharing data. That’s probably the reason for the steep demand for ransom. Cr1ptT0r is new to the market, but it looks like a long stay is planned. It is designed for Linux systems with a focus on embedded devices, but according to its maker, it can also be adapted to Windows. The end game makes money and, as someone familiar with this type of business told us, the return on investment can be almost infinite. The malware does not currently have a significant presence, but it could become a disgusting threat.