These forms of cyber attacks have many functions, including:
Tricking recipients to share their personal/financial information, redirecting targets to spam websites, or tricking them to download attachments infected with malware.
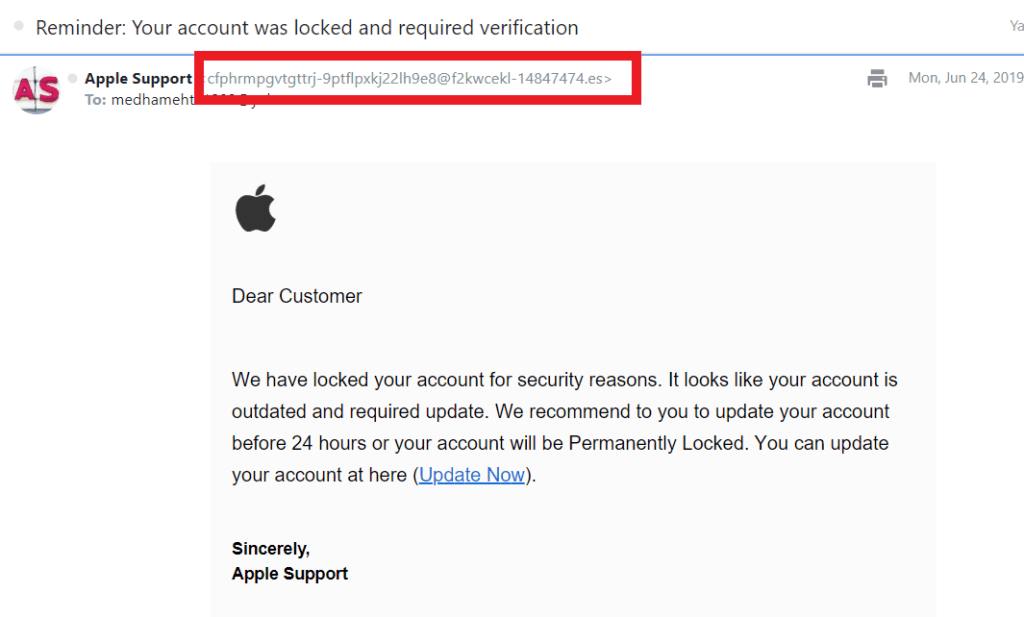
An example of a phishing email that I got is below:
The intruder is impersonating the support team of Apple in this email to try to trick me into clicking on a malicious connection. Apple Support signs the email and also contains the logo of the organisation, which could be necessary to fool certain email recipients. But in neon lights, there are two main details that scream “DANGER”: the email address of the sender and the badly written post. If Apple legitimately sent the email, it must have originated from an email registered with the domain apple.com, not a bogus account like the one seen above. In addition, they wouldn’t give “Dear Client” a note, they’d call you by name. And they will surely not send an email that is filled with grammatical mistakes!
DDoS Attacks
DDoS attacks are a significant threat that can impact anyone from small firms to big companies. In 2019 alone, NetScout Threat Intelligence saw 8,4 million DDoS threats. Attackers bombard a target with multiple requests concurrently in a distributed denial of service attack (DDoS attack). A server, a network, a service, or a website may be targets. The unforeseen heavy traffic (or an influx of packet forwarding) overwhelms the target’s server during a website DDoS attack, for example, and the website becomes sluggish or avoids reacting. What makes these kinds of cyber threats so devastating is that they interrupt the services of the intended website, rendering them inaccessible to legal users. Scripts or toolkits that build botnets are used by attackers to produce traffic from various sources. That’s why blocking any single user/IP address makes it hard to avoid DDoS attacks. In certain cases, to stop the attack, the attackers can demand a ransom from website owners. Some common explanations for attacks against DDoS include:
Harming the image of a corporation or domain, causing financial damage due to downtime on the website, or taking personal vengeance against the owner of the site.
Botnet Attacks
The word “botnet” refers to a computer or related system network. Here, a vast number of IoT computers are compromised by attackers and their combined capacity is used to perform numerous forms of cyber attacks. Even if one form of botnet attack is also a DDoS attack, it’s not the only one. Other types of botnet attacks include, according to Akamai, those that involve:
Validate lists of stolen passwords that lead to account takeovers (credential-stuffing attacks). Attacks on web apps to steal data. Giving access to a computer and its connection to a network to an attacker.
To build a botnet, attackers use phishing emails and malicious websites to inject botnet malware (such as trojans, computer viruses, etc.) into the computers of users. Other infected hardware or IoT systems may also be used by them to infect other devices on the same networks. For instance, once infected with Trojan malware, the system takes instructions from a command-and-control (C&C) server and performs cyber attacks as ordered by the botmaster. The device owners do not know that their computers are being used to carry out cyber threats when all of this occurs. In 2019, Spamhaus Malware Laboratories saw a rise of 71.5 percent in Botnet C&C over the previous year. Here are a number of important things to remember about botnets:
It is important to link all the devices used in a botnet to the internet. In order to include them in a botnet, attackers can infect PCs, notebooks, cell phones, WI-FI routers, tablets, internet-connected televisions, cable set-top boxes, DVRs, VoIP devices, and IP/CCTV cameras. To encrypt their internal messages, some botnets use PKI. Which means, without a corresponding private key, no one can track and detect their messages. It makes it very difficult for safety tools to identify and delete the botnet. Many goals and aims are fulfilled by botnets. Botnets are also widely used for crypto mining, data stealing, creating false web traffic, and distributing malware, in addition to the forms of cyber attacks we mentioned earlier.
Brute Force Attacks
In brute force attacks, in order to enter a system/site/user account, attackers seek to locate the right login credential. Attackers have a pre-guessed login credentials folder. They inject a script that automatically adds usernames and passwords to the login page of a target website before it finds the right combination. The attackers attempt to hack into users’ accounts, webmasters, main employees of the organisation, or website administrators. Two key forms of brute force attacks are available.
- Username Stuffing: The script dynamically adds several variations of user IDs and passwords to locate the valid combination in the targeted login fields. In addition, the intruder obtains those databases from leaky databases or instances of data breaches.
- Spraying passwords: The intruder tries a single password against several user accounts here. In other words, before attempting another password, the attackers “spray” the same password across several user accounts. A brute force attack is often used by attackers to manipulate URL access bugs to identify secret web pages. Let’s take the case below: Assume that my hospital shares a customised page that looks like this to read my information online: www.myhospital.com/patientreports/July2020/report0235683. To see my reports without any credentials, I just need this connection. Yet I understand that my report/file number is “report0235683.” So, if I write “report0235684” with the same URL, I can view the reports of the next patient! An example of a form of cyber attack that can lead to a data breach is forced browsing. To bypass such vulnerability flaws, attackers use brute force attacks. To find such secret and vulnerable websites, they use scripts to create random URLs. Attacks by brute force are useful for:
Stealing sensitive information, putting unnecessary ads on the page, Transferring money, making transfers on behalf of hostages, and locking down the ransomware attack networks of targets.
Attackers often sell the right pairs of user IDs and passwords to other offenders on the dark web. To make a profit or to cause general mischief, they can do this.
Man-in-the-Middle Attacks
It’s known as a man-in-the-middle (MitM) attack when an intruder eavesdrops, interprets and modifies the conversation between two endpoints. All sides believe they speak openly with each other and are oblivious that their connection is being infiltrated by others. Hackers bypass WI-FI router authentication bugs and/or the protection function of the website. Suppose you choose to order a pair of shoes on an e-commerce website. During the checkout process, you provide your credit card numbers, phone number, physical address, and email address to the website. But a hacker intercepts the data in transit before the knowledge hits the planned website’s server. As a consequence, the details can be read by the hacker (i.e. the guy in the middle) and used to commit financial fraud and identity-theft related crimes. They will still use it as part of their security questionnaires to view any accounts that use the information. Meanwhile, before it’s too late, you and the website you’re linked to are unaware of what’s happening.
Man-in-the-Browser Attacks
Attacks by Man-in-the-browser (MitB) steal messages between browsers and visiting websites. To do this, an attacker introduces a trojan horse into the web browser via a browser plugin, script, or browser helper object (BHO) to infect it. After the trojan is triggered, the attacker can:
Modify/add/remove fields in the context of pages, Adjust the website’s presence, Read and snatch any data entered on the website by users, and alter purchases made by users of the site.
MitB Trojans are so strong that the responses, responses, and validation receipts coming from the end of the website can also be updated. Before the victim revisits the platform, they should even delete the whole transaction from the data! Users visit the legit website here, and thus, they suspect nothing. Apps, using their initial keys, render the exchange. As no authentication phase is circumvented, the website has little to be concerned about. MitB attacks, in particular on banking websites, are widely used against the financial industry. But it can take place on any other form of website, such as websites for e-commerce, utility providers, tax and accounting companies, government websites, etc.
Drive-By Attacks
When a consumer visits a malware compromised website that downloads and instals malware on the user computer, a drive-by cyber attack happens. Users can be abused by malware-laden applications in a number of ways, such as
Recoding and recording the actions of users Corrupting other connected devices for botnet construction Stealing personal and private details from consumers Sending phishing emails to email contacts of consumers
In one of the following instances, drive-by malware infects appliances:
Legit apps: Attackers inject malware with legal software, files, media, etc. Fake applications: Attackers substitute malicious fakes for real software and use descriptive domain names to deceive users to download them. Cybercriminals are suspected, for instance, to do this with bogus antivirus apps. Fake alert messages and prompts to update: Cybercriminals will show false warning messages that make you feel that your current applications or plugins need to be modified (such as your web browser or Flash). But now, malicious software is imported to your computer as you attempt to upgrade your new software. Links: The site can auto-download malicious software onto its devices without their knowledge or consent when users visit a website and click on a compromised connection. For instance, this can occur when an attacker places a malicious script on the “play” button of a video or the “download” button of a song. Spammy websites: Certain websites are so contagious that if a user hits them, drive-by malware instantly downloads.
Final Thoughts on the Different Types of Cyber Attacks We’ve Discussed
It seems like every year is another record-breaking year when it comes to the number of cyber attacks that take place. Now that you’ve read how different types of cyber attacks are prevailing in the industry, you’re likely wondering what can you do to prevent cyber attacks in the first place. In general, follow these basic tips to prevent different types of cyber attacks:
Be vigilant while engaging with links and attachments in questionable emails and websites. Be sure to read the email header information and hover over link text to verify the real links. Never download anything from the internet before scanning it with a reliable antivirus tool. Keep your software current and operating systems patched and up to date. Never share anything on websites that use the insecure HTTP protocol (i.e., websites that aren’t protected by SSL/TLS certificates). Manually check your download folder, C:/Program File, C:/Program Files (x86), and C:/Windows/Temp folders to identify any unwanted/unknown programs, files, and software. Use robust antivirus and anti-malware solutions. Network monitoring and endpoint security solutions are important, too. Always maintain multiple copies of your current data backups. If you’re a small business owner, follow the tips provided in this article to protect your business from different types of cyber attacks.