Most contemporary routers give the opportunity to divide the network into several separate sections. A guest network that operates parallel to the host is one instance. The border isolates delicate or critical systems from other systems that have less stringent security policies. This is a prevalent practice and even a suggested safety measure. However, it is a logical separation at the software stage and is not airtight.
Cross-network communication coverage
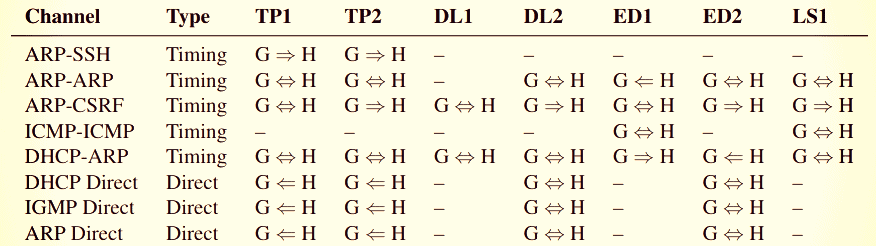
Researchers at Ben-Gurion University in Negev found multiple methods for transferring data on the same hardware across two segmented networks. They did this through covered direct or timing channels and tested the results on seven routers from multiple vendors in various prices. The techniques do not allow big numbers of information to be exfiltrated but demonstrate that the logical barrier can be breached. Clandestine direct communication is feasible by encoding information in packets which are misdirected to both isolated networks by various protocols. This method does not work on all tested routers and, in all cases, the transmission is not bidirectional. In order to send the data, time-backed covert channels depend on common hardware resources (CPU time, network and memory buffers). This is achieved by affecting the use and reading of those resources to interpret the data bits. “To exploit these [timing-based] channels, we need to construct sender and receiver gadgets which cause an increased demand on the router’s control plane or sample this demand, respectively.” The investigators tested TP-Link, D-Link, Edimax and Belkin equipment. Some of them are still supported, with Edimax BR-6208AC’s latest firmware update on 14 January 2019.
Trafficking information in lawful packet
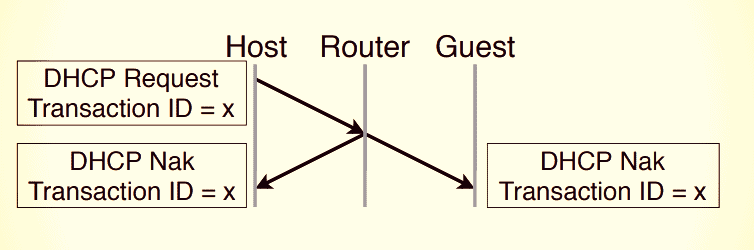
The router isolation architecture does not block direct communication via a covert channel. Limited permissions on the router are sufficient to exploit them via special network traffic which reaches both the customer and the host. Researchers have discovered that sending an invalid DHCP request message on some routers leads to a negative reaction (NAK) that is incorrectly transmitted to both the customer and the host network. DHCP is a management protocol which assigns IP addresses to machines connected to the router. DHCP (Dynamic Host configuration protocol). For this purpose, routers with an active guest network must be allowed. “The DHCP direct covert channel exploits the fact that some DHCP packets have an unusual IP header, which includes 0.0.0.0 and 255.255.255.255 as the source and destination addresses, respectively.” This enables data to be transferred to the other network by encoding in the 32-bit transaction ID field:
IGMP membership query incorrectly sent to both networks The Address Resolution Protocol (ARP), which allows the discovery of MAC addresses on the IP of the network, is another technique. If a client sends an ARP application for the machine’s MAC address with a particular IP, the answer with the required details is provided. Some routers send the ARP requests to the host and to the guest network as broadcast packets. This can be used for moving information, either in the bottom 8 bits or all 32 bits of the IP address, through the sending of a request to any computer on the network. “Direct covert channels can be considered software bugs, and are relatively simple to fix in software, either by the addition of additional firewall rules which block these data packets, or by scrubbing the sensitive data and replacing it with random data.”
Timing-based covert channels
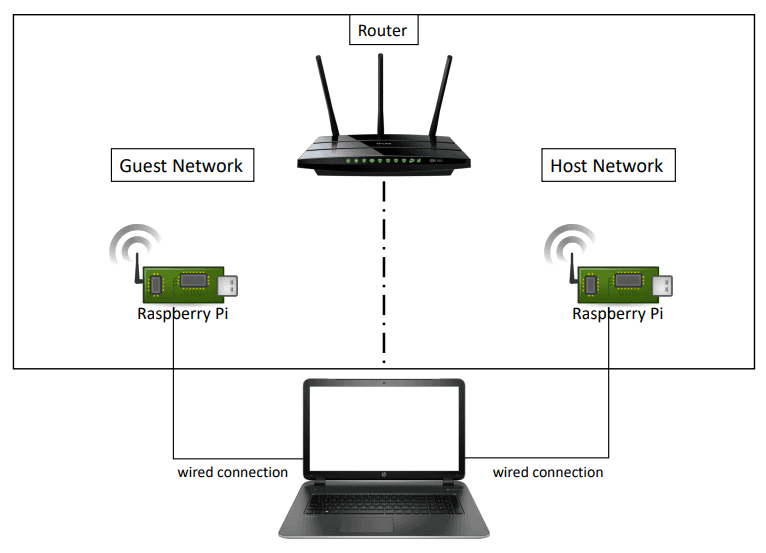
The benefit of communication of information in this manner is harder to avoid due to shared resources and an architecturally changed solution. The researchers used a Raspberry Pi computer with a wireless connection to a router’s host and guest networks for this experiment. One is the sender— it initiates the increased demand for resources and the other is a recipient. Both mini-computers use a wired connection to a laptop that initiates and collects measurements.
An indirect covert channel has been created by creating a CPU-intensive SSH link (Start using free ssh vulnerability scanner online to prevent from hacker.)with an aborted key exchange. The method slows down the reaction of the router to other demands and allows measurement. The scientists minimized the calculation time by selecting a lower key size to boost the bitrate. Cross-site request forgery (CSRF) operates on certain routers because of the host’s exposure of the Web management interface. The browser protections do not permit altering router configuration through a CSRF attack, but an iframe integrated in a web site can still be used to view content from another website. A loaded iframe raises the CPU load several times enough to be measured by the receiving RPi. ARP packets are also appropriate for information exfiltration of this kind, as various ARP queries affect the utilization of the CPU. The sending of numerous queries from one network delays the answer to an request from the other network to measure the response time. DHCP also operates for covert interaction based on time, although operations produce logs on the device. As additional system activity improves DHCP transaction processing time, an intruder can determine how long the router takes to answer a lawful application. Blasting ping commands can function as efficiently as for ARP, tell scientists; and the ICMP (ICMP) used for these commands is probably activated by the guest network of other router designs.
Outcomes, silence, and CVEs
The findings from the experiment differ from hardware to hardware:
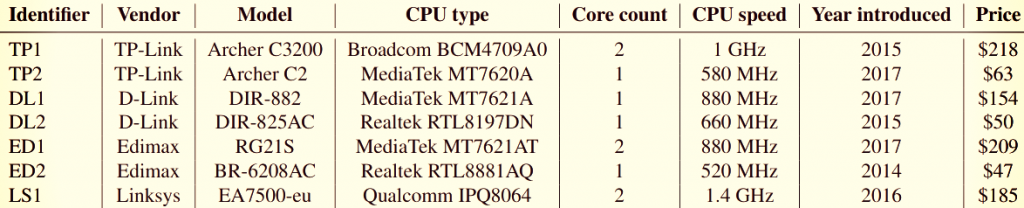
TP1 = TP-Link Archer C3200 (end-of-life) TP2 = TP-Link Archer C2 (end-of-life) DL1 = D-Link DIR-882 – (latest firmware release: March 9, 2018) DL2 = D-Link DIR-825AC – ? ED1 = Edimax RG21S – (latest firmware release: May 25, 2018) ED2 = Edimax BR-6208AC – (latest firmware release: January 14, 2019) LS1 = Linksys EA7500-eu – (in support, latest firmware release: November 11, 2018) In May, manufacturers of equipment used for this study were notified of these outcomes. Only Belkin’s safety reaction team responded that they had no intention of fixing vulnerabilities. However, the failures identified by the scientists got the following identification figures and are monitored as:
CVE-2019-13263 CVE-2019-13264 CVE-2019-13265 CVE-2019-13266 CVE-2019-13267 CVE-2019-13268 CVE-2019-13269 CVE-2019-13270 CVE-2019-13271
Adar Ovadya, Rom Ogen, Yakov Mallah, Niv Gilboa and Yossi Oren are the researchers involved in the experiment. Their results can be found in the document titled ‘ Cross-Router Covert Channels ‘ which was published in the 13th USENIX Workshop on Offensive Technologies (WOOT ‘ 19).