But how do you actually know the VPN you’re planning to use or currently use is actually protecting your traffic? How do you know the provider isn’t just lying about all the security they offer? It sounds a bit paranoid, we’ll give you that, but it often pays to be very skeptical nowadays. Otherwise, you might end up using a VPN that monitors and sells your data to advertisers, or a service that sells your bandwidth to the highest bidder. If that has you a bit spooked, don’t worry – we’ll show you what you can do to really test a VPN’s security to make sure it doesn’t put your privacy at risk. So let’s get started:
“Test” Its Privacy Policy
Okay, this might feel like we’re cheating since you can’t actually use an app to test the Privacy Policy. And because by “test,” we mostly just mean reading the policy. But this is still a really good way to check if the VPN takes your privacy seriously or not. Basically, you have to answer one question – do they keep logs? If they do, that’s a red flag. If you see any mention of “usage logs,” run for the hills. That pretty much means the provider will logs everything you do with the VPN – what sites you visit, what web apps you use, and what files you download or upload. Really, it’s like you’re not using a VPN at all. If the Privacy Policy only mentions “connection logs,” that’s still a problem. While those logs mostly store data needed to troubleshoot services, they can also track your IP address. Again, that’s pretty pointless. You’re using a VPN to hide your IP in the first place, after all. So only a zero-log policy makes sense if you want to enjoy true Internet privacy. If you’re not felling up to reading an entire Privacy Policy, though, there is a shortcut – this guide from ProPrivacy to the best no logs VPNs that you can trust.
Test the VPN for Leaks
A VPN leak is when your IP address and DNS queries leak outside the VPN tunnel. Basically, it’s as if you’re browsing the web without using a VPN at all. Websites and hackers can still see your real IP address, and your ISP still knows what sites you like to visit. So you should definitely test the VPN for leaks. If it offers a free trial period, take advantage of it and do it then. If not, do the tests while you’re still eligible for the money-back guarantee. Now, VPN leaks come in different types – IPv6, DNS, and WebRTC. Luckily, there’s an online tool that lets you test for all of them in one go: ipleak.net. Here’s what you need to do: If you see that your original IP and DNS addresses still show up, the VPN is leaking them. If you’d like a more in-depth approach, you can use these tools to test for each type of leak individually:
IPv6 leaks – IPv6 Leak Tests DNS leaks – com WebRTC leaks – WebRTC Leak Test from BrowserLeaks
Test the VPN for Malware
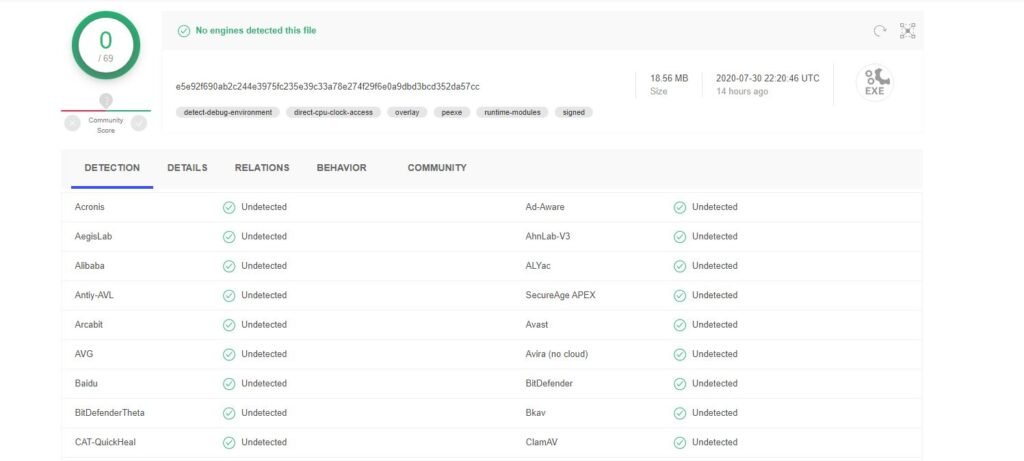
Yes, it’s true – unfortunately, some VPNs might actually expose you to malware when you download and use their apps. Luckily, that’s mostly the case with free VPNs. So you don’t really need to worry about this if you use a paid service. Still, that doesn’t mean you shouldn’t test the apps before you download them. Even if the provider doesn’t have any malicious intent, who’s to say a cybercriminal didn’t manage to silently compromise their code? That’s quite a stretch, we know, but it’s better to be safe than sorry. Plus, testing a VPN app for malware only takes a few seconds. Just use VirusTotal, and copy-paste the download link or upload the VPN installation file before launching it. Here’s our result with one of NordVPN’s apps. Green is exactly what you’d want to see.
Besides doing this, you should also install antivirus protection on your device. If a malicious app manages to slip by or you forget to test it before launching it, you’ll have an extra layer of defense.
Test the VPN’s Encryption
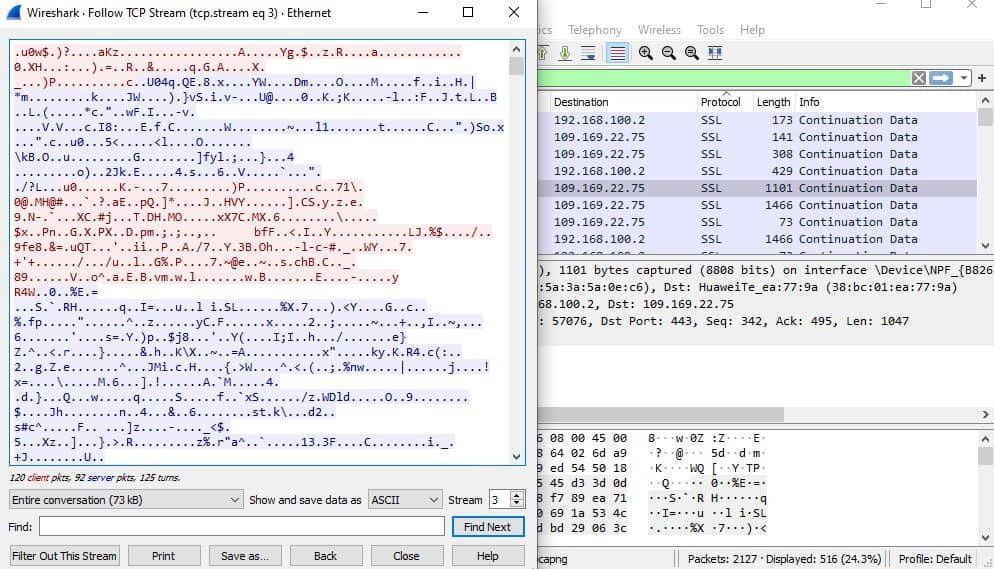
Sure, the VPN says it offers “military-grade encryption,” but just how true is that? Well, there’s only one way to find out – you test the VPN connection to make sure the traffic really is encrypted. The best way to do that is with Wireshark – a free tool that monitors network traffic. Here are the steps you need to follow: Here’s an example of VPN encryption that works:
A More User-Friendly Alternative
If Wireshark is a bit too intimidating, you could use Glasswire instead. Here’s what you need to do: Here were out results with Surfshark’s client. As you can see the majority of the traffic is classified as SSL/HTTPS.
How Else Could You Test a VPN’s Security?
If you know other things worth checking out and testing to make sure a VPN can really keep your data safe, please tell us about them in the comments.