Spyse, a new cybersecurity search engine, has recently combined all their products into a single service which offers mass data on various internet elements: networks, companies, vulnerabilities, and more. With this tool, security specialists, pen-testers, and bug bounty hunters can dramatically accelerate the process of gathering data. Utilizing a database approach, Spyse pre-gathers data to make it available to all users instantly. With a service like this, security personnel can seal vulnerabilities on time and keep cyberpunks off their business’s infrastructure.
Read on to learn more about this excellent new service.
How Spyse Collects Data?
Spyse employs a database where all data is stored before being made available. By giving users instant access to information, which is usually tedious to obtain, loopholes, errors, and bugs can be fixed promptly, thus preventing most forms of cyberattacks. To maintain the database, Spyse implemented self-developed scanners that run a process of uninterrupted data gathering. Data is then compared to other sources to ensure authenticity, before being stored, analyzed, and presented to the user upon request. Spyse also implements a distribution system consisting of 50 servers, cleverly placed around the globe to bypass location scanning restrictions and ISP blocking. As a result, the Spyse search engine will always present broader amounts of data than random online scanning tools.
Spyse Database
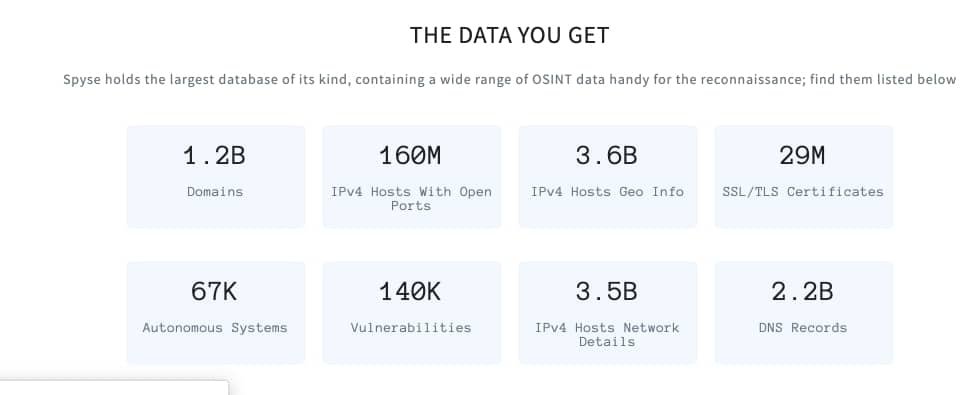
In reconnaissance, the most tedious process is collecting data. Mostly because of the time it takes for various services to retrieve the data and send it back to the user. Alternatively, Spyse proposes a ready-database where mass data is stored. The database is a crucial feature of the Spyse search engine. In essence, 50 fastest and most reliable servers storing hot data (over 7 billion documents) create quick access to any information collected by Spyse scanners. Pre-storing data also allows Spyse analyzers to process it, visualizing relationships between different internet elements. This enables users always to find additional data connected to their primary target, and opens up more possibilities in identifying more possible vectors of attack.
Presentation of Data
Spyse offers two ways of using data: via the web interface and the API. The web interface allows users to extract aggregated and structured information in a handy format with blocks of data. These blocks (or tables) can be physically moved around for convenience, and data inside can be filtered for precision. Users can also download all found data as long as they’re subscribed to the service. If the web interface feels somewhat limited, users can access the API. The documentation for the API was made with Swagger, which offers easy understanding and lots of flexibility when extracting necessary data. The API can be easily integrated into various tools and services and is an excellent alternative while the team has yet to reveal their CLI. Users can also try the Python wrapper made by the outsourced developer zer0pwn.
Advanced Search and Security Scoring
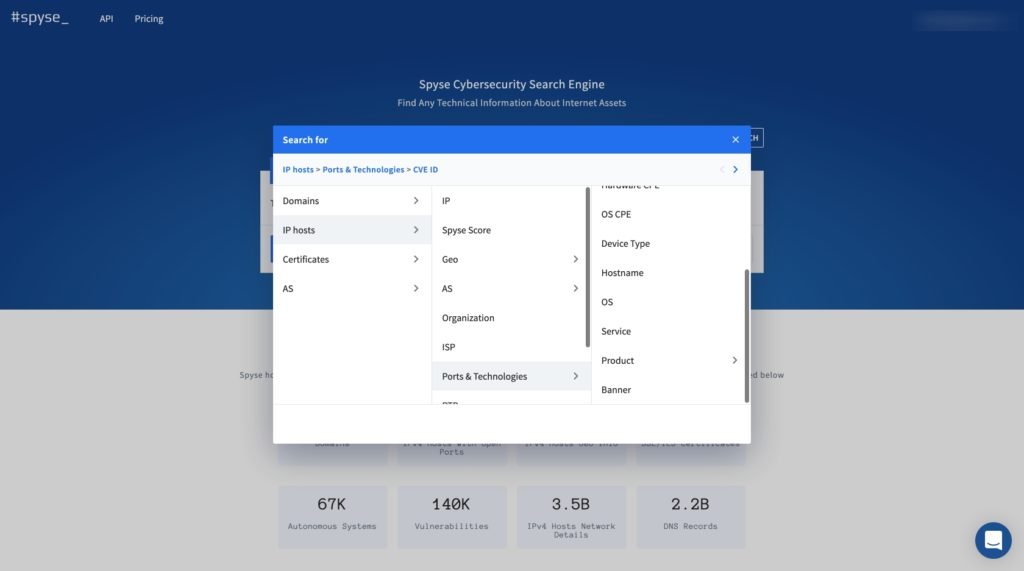
There are two more tools that further enhance the Spyse search engine experience of gathering precise data: Advanced Search and Security Scoring. Advanced search lets users place up to 5 search parameters per single query. This helps narrow down the question and avoid the process of visually analyzing thousands of lines of data. With the ASN lookup and just a few parameters, users can find all sites, servers, and even databases related to some organization, detect their vulnerabilities, and help to expand the target area by showing relationships with other internet elements.
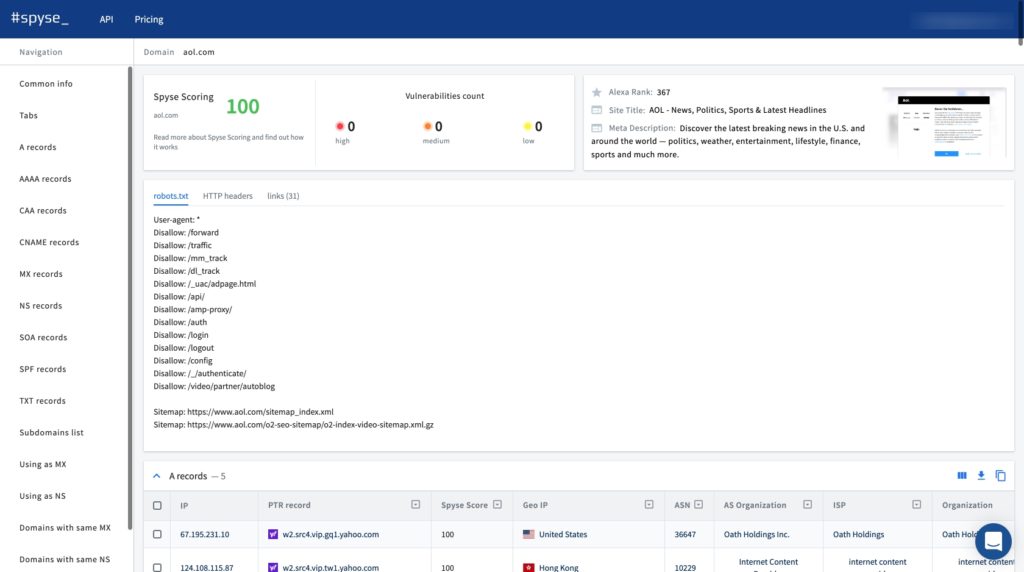
Security scoring is another useful tool that can help establish and filter through a list of vulnerable (or well-protected) target networks or infrastructures. Taking all information from Spyse scanners and connecting it to the CVE, Scoring provides an overall security rating for a system, scoring it on a scale from 0-100. Users can also view the details of found vulnerabilities, including CVSS 3.x, and CVSS 2.0, impact, exploitability, attack vectors, references, and much more.
For All Cybersecurity Personnel
With Spyse, system administrators can monitor the security levels of their cyberinfrastructure uninterruptedly. Sysadmins attain information straight from a database, which can be done manually or by writing a few basic scripts. In this way, analyzing security levels of networks or infrastructures to find vulnerabilities and potential entry points is made much easier and more convenient. Pentesters and bug bounty hunters will also find great uses for Spyse’s search engine. Using the service can help them gather target information much quicker and create a target list. Spyse solves most problems related to information searches such as time, rate limits, and staying unnoticed while digging for data. Overall it’s a great resource to use when other resources are forbidden by the contract or bug bounty agreement. Overall, Spyse’s cybersecurity search engine is a time and resource saver, overseeing all processes of information gathering and enabling security personnel to do their job at the highest standards.